what must be done in order to appropriately secure user data across all platforms
Data security is one of the most daunting tasks for IT and infosec professionals. Each year, companies of all sizes spend a sizable portion of their Information technology security budgets protecting their organizations from hackers intent on gaining access to data through animate being force, exploiting vulnerabilities or social engineering. Throughout this guide are links that will assistance y'all learn more about the challenges related to securing sensitive information, ensuring compliance with government and industry mandates, and maintaining customer privacy. Along with the challenges, yous'll find advice on how to solve them.
Why data security is important
The average cost of a data alienation in 2019 was calculated at $3.92 million, according to a report by the Ponemon Establish and IBM Security. Loftier-profile companies such as Capital 1, Evite and Zynga experienced data breaches that exposed more than 100 meg customer accounts each. The average security incident in 2019 involved 25,575 accounts, according to the report. To brand matters worse, this information must be disclosed to customers, and organizations could potentially air current up as cautionary tales.
The lessons from these breaches are numerous, including the need to do the following:
- review credential requirements and policies;
- proceed track of what data is retained and where it is stored;
- bank check for cloud misconfigurations regularly; and
- force password resets if a alienation is suspected.
The move to the cloud presents an additional threat vector that must be well understood in respect to data security. The 2019 SANS State of Cloud Security survey found that 19% of survey respondents reported an increase in unauthorized admission by outsiders into cloud environments or deject assets, upwardly vii% since 2017.
Ransomware and phishing also are on the rise and considered major threats. Companies must secure data then that it cannot leak out via malware or social engineering science.
Breaches can be costly events that result in multimillion-dollar class activeness lawsuits and victim settlement funds. If companies need a reason to invest in information security, they demand merely consider the value placed on personal data past the courts.
Sherri Davidoff, author of Data Breaches: Crisis and Opportunity, listed five factors that increment the gamble of a information alienation: access; amount of fourth dimension data is retained; the number of existing copies of the data; how piece of cake it is to transfer the data from one location to another -- and to procedure information technology; and the perceived value of the information by criminals.
Many organizations realize that the value of information and the price to protect information are increasing simultaneously, making it near impossible to protect data by merely layering on more security. Instead, Information technology and infosec teams must think proactively and creatively near their data protection strategies.
They should likewise assess their chance versus the protections their current security investments provide and make decisions accordingly. To practise so requires an unprecedented level of visibility that most organizations do non possess right at present.
Security expert Ashwin Krishnan advised IT and security professionals to focus on three key aspects when trying to improve data security in the modern enterprise: the more data generated and collected presents a bigger "surface" for information breaches; customer rights expand with new regulatory compliance and privacy compliance mandates, such as GDPR and the California Consumer Privacy Human action; and companies have to be aware if they are involved in data brokering.
Types of information security
Data security has myriad aspects that protect data at balance, in motion and in use. Here are some technologies widely used by enterprises to protect data.

Encryption
One of the most basic concepts of data security is encryption, as simply encrypting sensitive data tin go a long style toward meeting privacy and compliance mandates and keeping sensitive information safe from hackers.
Encryption is not a 1-size-fits-all suggestion, every bit organizations must select the encryption algorithm that matches their enterprise security requirements. Our encryption tutorial deciphers the differences and helps y'all select the best approach for your arrangement.
The nigh common course of encryption -- symmetric -- involves converting plaintext to ciphertext using the same central for encryption and decryption. Asymmetric encryption uses ii interdependent keys -- 1 to encrypt the data and i to decrypt it. Symmetric encryption has many "flavors," including Avant-garde Encryption Standard and Triple DES. Disproportionate has the Diffie-Hellman cardinal exchange and RSA, among others. Companies that don't want to encrypt all their information must decide the priority of information through classification.
Perimeter security
Intrusion detection systems and intrusion prevention systems, along with access command lists, beef up an arrangement's security perimeter and reduce the severity of attacks that get through. Meanwhile, endpoint security direction can rails malware signatures and prevent them from causing damage. Networking expert Kevin Tolly explained the need for a multipronged arroyo to information security, also equally the unique traits of fast-and-frontal attacks compared to low-and-slow attacks.

Data loss prevention (DLP)
DLP prevents users from transferring sensitive data, and organizations can roll information technology out as enterprise security software. DLP tools tin can exist deployed as agents on endpoints or agentless at the network level. Learn how to choose DLP products as well as considerations for DLP deployment.
DLP software often includes templates to aid compliance with specific mandates, such equally HIPAA and PCI DSS.
A cloud access security broker (CASB) also performs DLP tasks and can help mitigate the threat to data in the cloud. CASBs actively intervene in user-to-cloud application sessions past intercepting session traffic, helping to monitor and enforce corporate security policies. CASBs scan data objects, such as files and documents, to ensure they comply with corporate standards and authorities regulations.
All-time practices for developing a information security strategy
Data security, frequently thought to be about the prevention, detection and mitigation tools an organisation uses, is just equally much about strategy and the implementation of best practices. A good showtime to developing a strategy lies in focusing on the following areas.
Governance, take chances and compliance (GRC)
Some companies use GRC every bit a framework for ensuring data security and privacy compliance. Governance refers to how a company uses information management systems and hierarchical controls to ensure adherence. Take chances management is the identification, analysis and response to potential risks. Compliance is the assurance of conformity to regulations and corporate policies when handling data. Integrated hazard management takes GRC a pace further to speed upwardly decision-making and functioning.

Insider threats
The human aspect -- or insider threat -- is oftentimes underestimated or even disregarded when companies develop a data security strategy. Privacy and risk direction skilful Sudeep Venkatesh said targeted phishing attacks and concern email compromise attacks, which are aimed at summit people in the organization, cause the nearly harm in terms of information loss. To combat this trend, companies should enact best practices that marry prevention and protection so that communication is secured and delivered to the appropriate person. If no action is taken, companies are left vulnerable to breaches initiated by an action taken by an insider -- whether malicious or accidental.
Social media
Social media is another vector users autumn prey to when it comes to inviting malware into the enterprise. For case, hackers volition take reward of users who search for "cheat codes" to admission third-party applications, such as games on platforms similar Facebook, for costless. The cheat codes tin exist Trojans that enable a bad thespian to control a device, install ransomware, activate the camera or microphone, and record keystrokes to steal passwords. Third-party applications are just i of many enterprise social media risks that should be monitored and mitigated.
Visibility and discovery
Organizations also stumble on the information governance front end when they are unable to locate critical data that lives in nooks beyond the enterprise. For instance, protecting data is a Herculean task when users tin download sensitive data onto their hard drives and out-of-sight of compliance tools. Government regulations and corporate standards are pushing companies to gain ameliorate visibility into how they are handling, storing and processing information.
Cloud-based data besides requires a discovery mechanism to ensure governance. Before deploying any projection into the cloud, Information technology and security teams should sympathise the data types that will be involved, and they should each exist categorized and assessed for run a risk.
Password hygiene
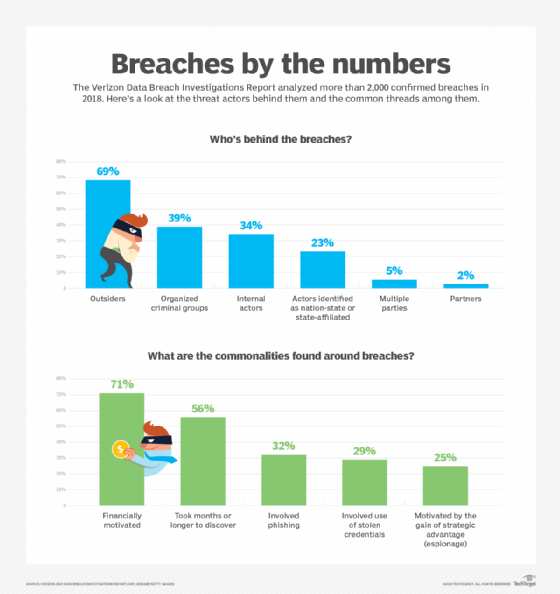
One of the more straightforward data security all-time practices is centered around passwords, which are a universal betoken of vulnerability for organizations. The 2019 Verizon Data Breach Investigations Written report establish that 80% of hacking-related breaches tin can be linked to stolen and reused credentials. Password spraying, keylogger attacks and other beast-force hacking techniques put on full brandish the weakness of traditional passwords. In addition, most users have far too many business application passwords to easily remember, resulting in poor password hygiene, which means not being unique enough or inverse often plenty.
Making passwords longer isn't necessarily the answer. They need to be more than complex or be used in conjunction with tokens, biometrics or other types of authentication. Users also tin can deploy enterprise password managers, which shop the encrypted passwords they employ across applications, to ease the burden of remembering every awarding's sign-on.
Database protection
Databases require all-time practices to secure the data within them as well. Iv simple steps can ensure sensitive information stays protected:
- Enforce the principle of least privilege where access is limited to what is needed to carry out a job function.
- Conduct regular access reviews to identify onetime and unnecessary permissions that could be compromised.
- Monitor database activity to discover unusual user activity.
- Encrypt sensitive data to protect it in transit and at rest to prevent snooping.
Data privacy and compliance standards
Developing, implementing and enforcing data security best practices is made easier if organizations fully empathise the privacy and compliance mandates to which they must adhere.

The California Consumer Privacy Act (CCPA) went into consequence January of this year. It enforces consumers' rights to control their personal information. Many experts believe a version of the CCPA will likely become federal law. CCPA itself is a take on the Eu's General Data Protection Regulation, which also protects consumers' personal data.
While companies worry that the cost to comply with government mandates could be prohibitive, many are all the same going forward in their efforts to ensure data is able to be discovered, reported on and erased. That way, when consumers asking to see their data and then delete it, businesses will be set up.
To follow the multiple compliance mandates, organizations tin create a data inventory, establish processes to get consumers their information nether deadline and make updates to the organization's privacy statement.
The hereafter of data security
AI and machine learning are going to exist key in compliance efforts going forward. Companies are looking to automate some regulatory compliance processes, including data location and extraction. Inventories, as security proficient Michael Cobb noted, become outdated unless automated scanning tools are deployed to sustain information discovery capture by recording regular snapshots of all applications and repositories where personal information resides. Automation, in his stance, is the just manner large organizations tin remain compliant with a large volume of information that is structured and unstructured and stored in data centers and in the cloud.
Adjacent-generation technology could also help companies fall in line with other compliance mandates, such as PCI DSS. For companies that have lagged backside on compliance, some security experts suggest considering a nada-trust model as a security strategy. With zero trust, companies would look at the total lifecycle of data direction and augment their focus beyond just payment carte du jour data to other forms of personal data, including fiscal data, intellectual property and client data. They would make no assumptions on where information is expected to exist constitute or how it is beingness used -- merely that the risk must exist mitigated.
Information security volition remain a significant challenge well into the future, but creative applications of AI and car learning and aught-trust models will help Information technology and infosec teams protect data and ensure consumer privacy.
Source: https://www.techtarget.com/searchsecurity/Data-security-guide-Everything-you-need-to-know
0 Response to "what must be done in order to appropriately secure user data across all platforms"
Post a Comment